
The Lazarus Group, which has ties to North Korea, has been implicated in the theft of almost $900 million of those revenues between July 2022 and July of this year. As much as $7 billion in Bitcoin has been illegally laundered through cross-chain crime.
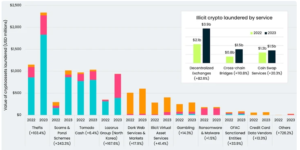
Blockchain analytics company Elliptic stated in new research released this week that “chain- or asset-hopping typologies are also on the rise” as traditional institutions like mixers continue to be the target of seizures and sanctions scrutiny.
Cross-chain crime is the practice of transferring crypto assets from one token or blockchain to another quickly in an effort to conceal their source, making it a profitable way to conceal the proceeds of cryptocurrency crimes and an alternative to Acc strategies like
The North Korean hacking crew is estimated to have stolen nearly $240 million in cryptocurrency since June 2023, following a series of attacks targeting Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), Stake.com ($41 million), and CoinEx ($31 million).
“The diversity, number, and eccentricity in implementation of Lazarus campaigns define this group, as well as that it performs all three pillars of cybercriminal activities: cyber espionage, cyber sabotage, and pursuit of financial gain,” ESET stated about the threat actor in the previous month.
The threat actor has also been connected to the deposit of more than 9,500 bitcoins via Avalanche Bridge, as well as the movement of some of the looted assets using cross-chain methods.
“As is evidenced by the assets ending up on the same blockchain on numerous occasions, these transactions have no legitimate business purpose other than to obfuscate their origin,” Elliptic said. “Bridging back-and-forth for the sake of obfuscation – i.e. ‘chain-hopping’ – is now a recognized money laundering typology.”
The disclosure comes as South Korea’s National Intelligence Service (NIS) has warned of North Korea attacking its shipbuilding sector since the start of the year.
“The hacking methods mainly used by North Korean hacking organizations were to occupy and bypass the PCs of IT maintenance companies, and to install malicious code after distributing phishing emails to internal employees,” the agency said.






